Introduction to DRM Development (1) Symmetric Key Cryptography, Asymmetric Key Cryptography and Hybrid Cryptosystem
I became interested in DRM (license activation) implementation while developing software, but the development was extremely difficult.
The most important reason for this was the lack of Japanese resources.
In this series, I will explain the development (mainly logic) of DRM as much as possible.
The first article will explain asymmetric cryptography, symmetric key cryptography, and hybrid cryptosystem.
This article is based on my understanding of them.
If you are going to use it in your business, I recommend that you consult an appropriate security expert.
What is encryption?
What exactly is encryption?
For example, imagine the following sentence sent from Mr. A to Ms. B via a friend.
Why don't we go out for dinner sometime?
Mr. A doesn't want his friends to know the contents of the message.
In this case, we need to encrypt the text in some way - specifically, in a way that only Mr. A and Ms. B know about - so that they can decipher it.
One simple form of encryption is called a Caesar cipher.
This is an encryption method in which the English letter E is shifted to B, D is shifted to A, and so on.
As an example, if the previous sentence were to be shifted one character at a time to the next, it would look like this
XIZ EPO'U XF HP PVU GPS EJOOFS TPNFUJNF?
This is the encryption.
This example is too simple, but it is possible to maintain some level of strength by complicating the encryption scheme, e.g. A is to C, C is to X, and so on.
What is symmetric key cryptography?
A symmetric key cipher is an encryption method where the same key is used by the encryptor and the decryptor.
AES and DES are typical examples of this type of encryption. Caesar’s cipher, mentioned earlier, is also a symmetric key cipher.
In AES cryptography, in addition to the plaintext, ciphertext and key, there are two more types: salt and iv. This is difficult for beginners to understand, so I will explain it here.
The salt is used to hash the key. This value must be unique to each user. The salt does not have to be secret.
The iv (initial vector) is used to randomise the ciphertext each time. It needs to be random.
This method has the advantage of low computational cost because it uses the same key, but the trade-off is that the key exchange must be done securely.
Diffie-Hellman key-sharing is often used for this key exchange, and this technology is also used in LINE's Letter Sealing. As this is very complex and my understanding of it is not up to date, I recommend browsing the LINE Engineering blog.
In short, the big disadvantage is that if the key is stolen, it can be both encrypted and decrypted.
What is asymmetric key cryptography?
Asymmetric key cryptography (aka public key cryptography) is an encryption method in which the encryptor and decryptor have different keys.
RSA is a typical example.
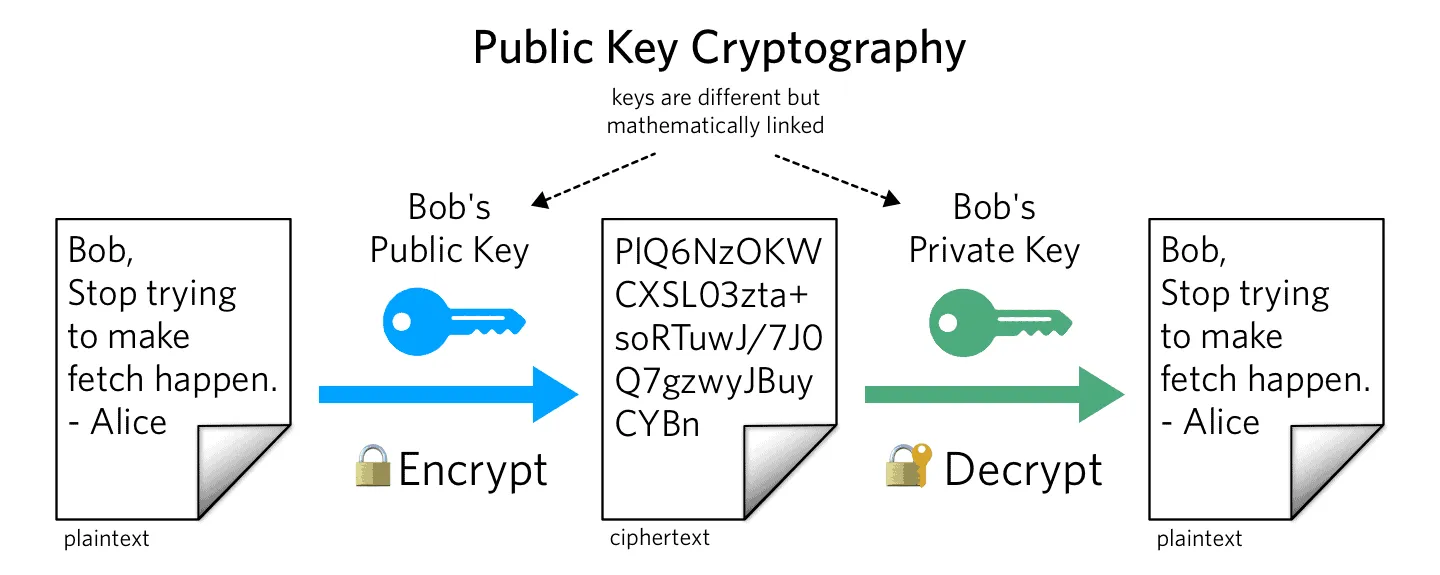
As the name suggests, a public key is essentially an encryption key only and cannot be used to decrypt any information, even if it were stolen by a third party.
In contrast, the private key is exclusive to the recipient and is completely separate from the public key. It is essentially used for decryption only.
To create a public key, you need a private key. In other words, if you have a private key, you can create as many public keys as you like. Therefore, the general flow is for the client to use the public key for encryption and for the server to use the private key for decryption.
As we will see in a later section, it is possible to see and modify the text and logic inside the software using a technique called reverse engineering.
Therefore, passing the private key to the client for decryption is a major security risk.
The solution to this is hybrid cryptosystem.
What is hybrid cryptosystem?
Hybrid cryptosystem, as the name suggests, is an encryption method that combines a symmetric key encryption with a public key encryption.
The term SSL/TLS for HTTPS will sound familiar to you. -> It's not. Thanks @angel_p_57 for correcting my misunderstanding.
In this method, the ciphertext and key are transmitted in the following flow.
- Sender creates common key A
- Encrypt the plaintext with its common key A (=ciphertext A)
- Encryption of the public key with a prepared public key (=encrypted key A)
- Send ciphertext A and encrypted key A to the recipient
The flow of the recipient of the cipher is as follows
- The receiver decrypts the transmitted encrypted key A using the private key
- The decrypted key is used to decrypt ciphertext A
This hybrid cryptosystem has a number of advantages, but two of the biggest ones are the following.
Firstly, the sender creates the key. Scondly, the key is encrypted with a public key.
This makes it relatively safe to exchange keys.
Conclusion
In this chapter I have described encryption methods.
It is very difficult to break a proper encryption and it takes tremendous time to analyse it with the average modern computer.
Still, it is important to note that it is much easier to break the logic before and after the encryption than it is to break the encryption.
This will be explained in the next section.